A client is beginning to build out its infrastructure into the cloud. Their parent company has an agreement with Microsoft and I have a decent size role in migrating services into an Azure subscription. We are focusing primarily on site replication and recovery, but we have a few services such as SQL databases and web servers that are in production.
We currently have an F5 appliance establishing an IPSec tunnel to Azure. We used the F5 because it was available, not heavily utilized, and supported IKEv2 which is required by Azure. We would have typically built the tunnel on a Cisco ISR, but ours are getting old and do not support IKEv2.
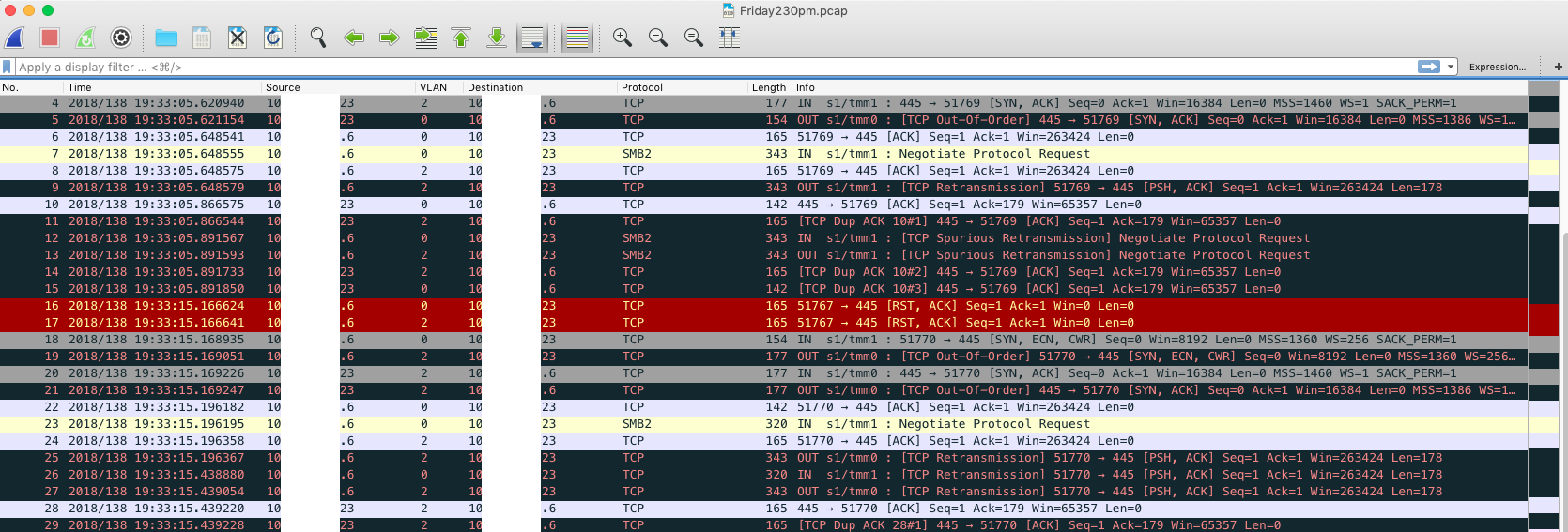
The only difficulty in setting up the tunnel to Azure were the multiple interfaces in separate VLANs used for load balancing and pools. If a network device was connected to one of those VLANs and tried to communicate to Azure, it used its default route, hit our core, and then went to the F5; but the F5 would take the response from Azure and send it directly to the device over the connected VLAN interface. So this obviously broke TCP/IP with traffic routing two different ways. I’m trying to find the technical term for this type of routing, and I will update when i do.
We added the F5 Wireshark plugin and noticed the traffic being on separate VLAN than when it originated.
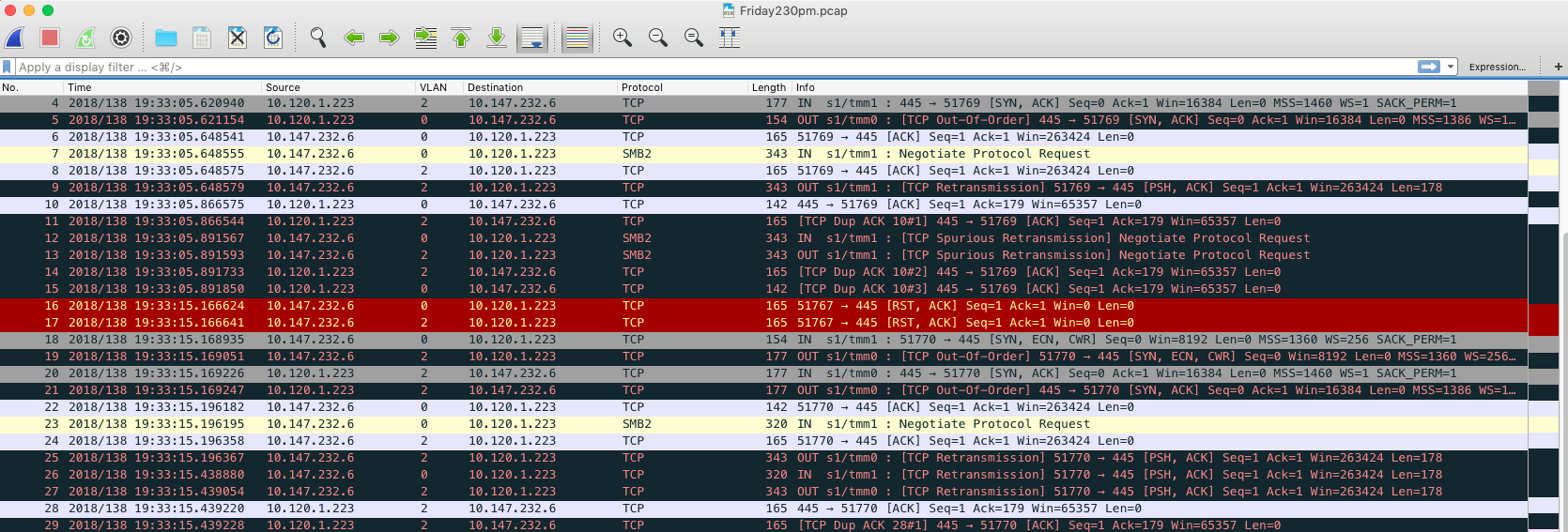
We were able to resolve the above issue with using Route Maps in our core.